Companies are spending an increasingly large portion of their budgets each year to protect themselves against cyber threats, and for good reason: cyber crime represents the 3rd largest economy in the world, after the US and China. Yet many never actually test whether they can withstand an attack, and over 73% of SMBs still report being compromised by a cyber incident over the past year.

What is Penetration Testing?
Penetration testing is a way for you to make sure your business is secure, by carrying out a controlled attack against your network to expose any vulnerabilities that hackers could use against you. Network penetration testing is a proactive security practice in which cybersecurity professionals, trained in the skills used by hackers, thoroughly and aggressively attempt to expose weaknesses in organization's networks and systems. This ethical hacking exercise simulates real-world cyberattacks to identify vulnerabilities before malicious actors can exploit them. An exhaustive report, detailing every aspect of your digital footprint, is generated that reveals where you’re vulnerable, and the exact steps you need to take to secure your network.
Who Needs Penetration Testing?
Any company with a network or online presence can benefit from penetration testing. Regular penetration tests empower organizations to anticipate threats and maintain a resilient security posture. In certain industries, however, such as finance, government and health care, penettesting is required for compliance and cyber liability insurance.
Presented are some industries with penetration test requirements.
- Finance
- Manufacturing
- Health Care
- Technology
- Government
- Education
- Oil & Gas
- Investment
- Insurance
- IT Services
Why Choose Two Fish?
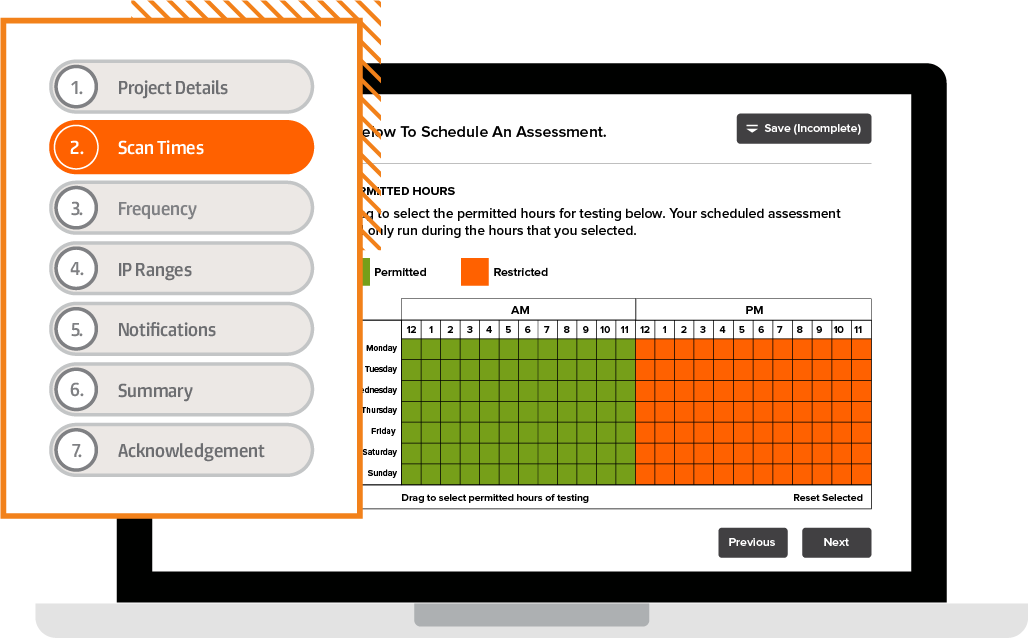
Two Fish conducts regular network penetration testing, such as quarterly or monthly, which allows you to stay at the cutting edge of threat protection and prevent catastrophic breaches.

Compliance
Our solution aligns with regulatory compliance requirements and cyber insurance requirements for network penetration testing.